Introduction
Watch our AI-generated introduction to the Intelligent SOC Ecosystem
This video was generated by NotebookLM AI. Content may contain inaccuracies and is for reference purposes only.
An Intelligent SOC Ecosystem for Monitoring, Detection, and Response to Cyber Attacks
Watch our AI-generated introduction to the Intelligent SOC Ecosystem
This video was generated by NotebookLM AI. Content may contain inaccuracies and is for reference purposes only.
An Intelligent SOC Ecosystem for Monitoring, Detection, and Response to Cyber Attacks
A unified Intelligent SOC Ecosystem where SIEM, SOAR, OpenXDR, Threat Intelligence, and AI/ML/LLM platforms are integrated into a cohesive operational pipeline. The system enables end-to-end security event processing: from log collection and normalization to analysis and automated incident response. SmartXDR serves as the intelligent fusion layer, providing semantic analysis, event enrichment, and risk-based triage prioritization.
 MITRE ATT&CK
MITRE ATT&CK
Cutting-edge technologies powering our project
Complete search and analytics platform
 Elasticsearch
Elasticsearch
 Logstash
Logstash
 Kibana
Kibana
 Beats
Beats
 Elastic Agent
Elastic Agent
 Elastic Fleet
Elastic Fleet
 pfSense
pfSense
 Suricata IDS/IPS
Suricata IDS/IPS
 Linux Router
Linux Router
 Zeek - Network Security Monitor
Zeek - Network Security Monitor
 Windows Events
Windows Events
 Linux Syslogs
Linux Syslogs
 WAF Logs
WAF Logs
 Firewall Logs
Firewall Logs
 IDS/IPS Alerts
IDS/IPS Alerts
 NSM Alerts
NSM Alerts
 n8n Workflows
n8n Workflows
 DFIR-IRIS
DFIR-IRIS
 MISP
MISP
 IntelOwl
IntelOwl
From detection to response - seamlessly integrated
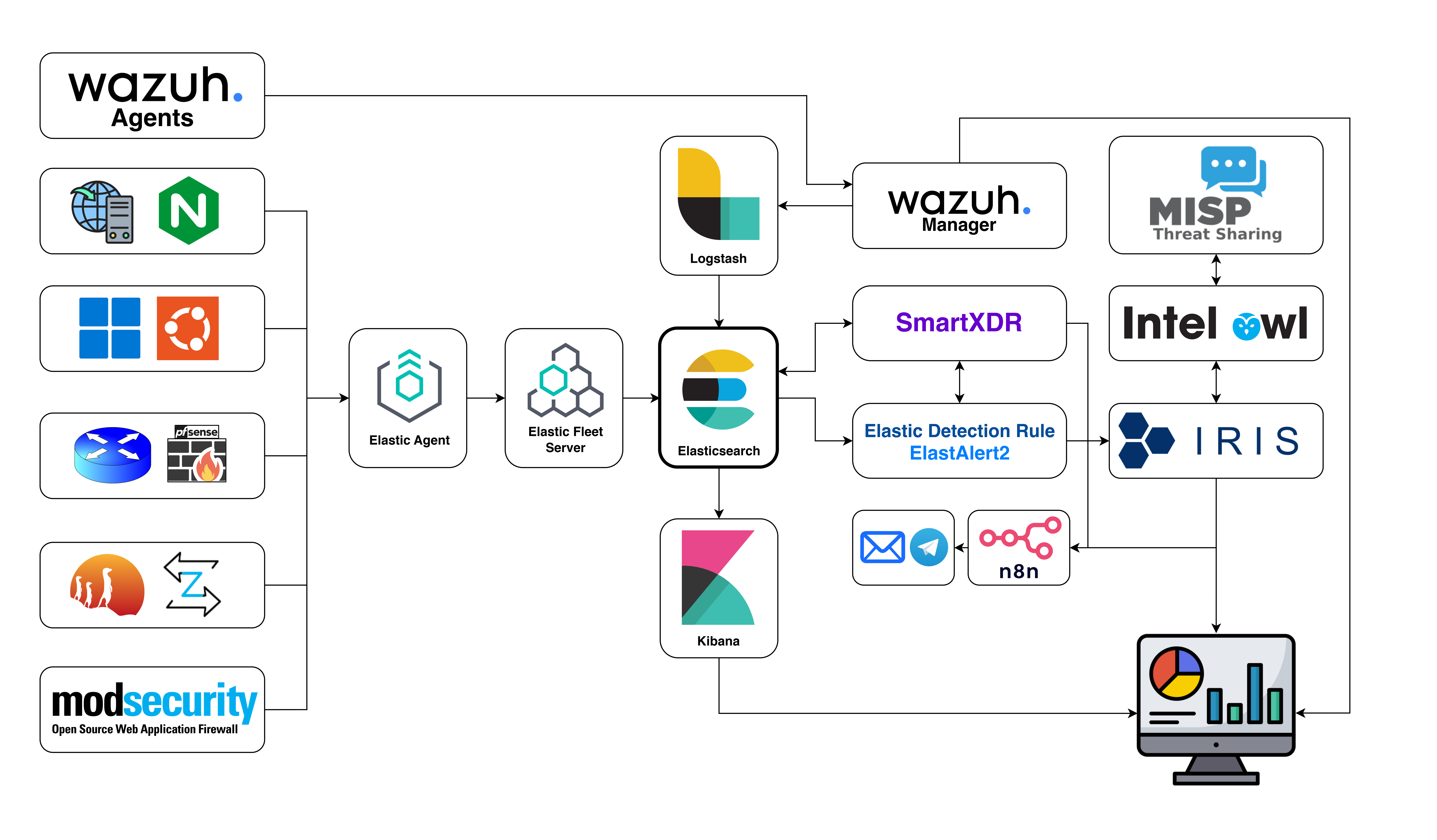
Network Sensors (Suricata IDPS, Zeek NSM), Endpoint Sensors (Wazuh Agents), and Network Infrastructure (pfSense Firewall, Nginx Reverse Proxy, WAF) provide comprehensive visibility.
Logs Management (Logstash, Elastic Agents, Fleet) normalizes data to ECS format. Elasticsearch serves as the centralized Data Lake for fast retrieval and long-term Big Data storage.
Kibana (SIEM Dashboard), Wazuh Manager (Security Management), Elastic Detection Rules (KQL/EQL), and ElastAlert2 provide real-time analysis and multi-layer alert generation.
n8n (Integration Hub), DFIR-IRIS (Incident Management), MISP & IntelOwl (CTI Platform), and SmartXDR (AI-powered analysis, automated reporting, human-in-the-loop decision support).
Intelligent SOC Ecosystem Core - The proposed solution designed as the central brain orchestrating the entire SOC operational pipeline
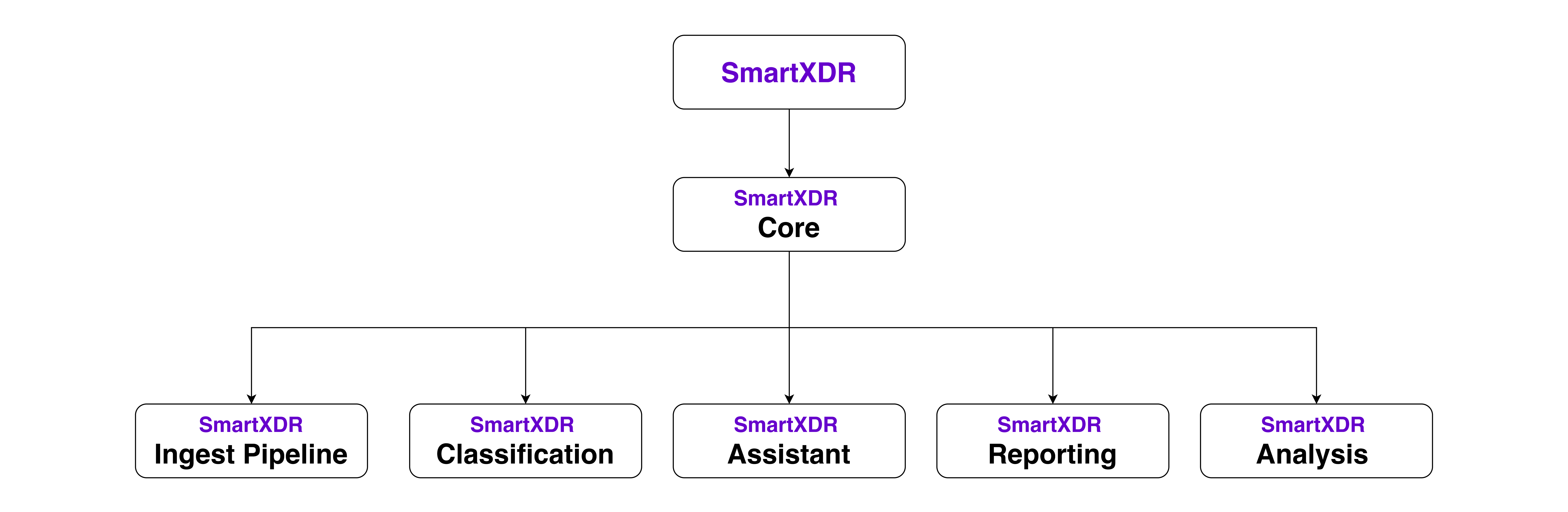
The central Control Plane responsible for orchestrating all modules, routing data, managing background tasks, and providing AI/LLM/RAG services. Includes API Gateway (Flask + Gunicorn), Re-ranking RAG with ChromaDB, Redis cache, conversation memory, and RBAC authentication with rate-limiting.
Handles data enrichment before storage by receiving ECS-compliant logs from Logstash, Elastic Agents and Fleet.
Custom-designed pipeline filters noise, extracts contextual information, and generates the ml_input field
as standardized input for SmartXDR ML Classification.
Uses Bylastic - a pre-trained DistilBERT model by Byviz Analytics - optimized for Elastic ecosystem.
Automatically classifies logs into INFO, WARNING, and ERROR severity levels by analyzing ml_input semantics,
providing prediction_probability scores for confidence assessment.
Deep analysis layer performing semantic analysis on Logs and IoCs. Features alert aggregation with Risk Score (0-100) calculated via multi-factor algorithm (Severity Distribution, Attack Escalation, ML Confidence). Integrates LLM+RAG for CTI-style reports and DFIR-IRIS for IoC enrichment via VirusTotal and MISP.
Extracts and aggregates classified log events to generate administrative reports from Elasticsearch and ML Classification results. Supports automated periodic reports and detailed triage reports by log source, distributed via Email/Telegram and Webhook with cloud storage upload for auditing compliance.
AI Security Assistant combining LLM with Advanced RAG using Two-Stage Retrieval: Bi-encoder Semantic Search (ChromaDB) for candidate filtering, and Cross-encoder Re-ranking for precision. Features MMR diversity optimization, Dynamic Thresholding, Token-aware Windowing, and MITRE ATT&CK mapping via Telegram Bot and API/CLI interfaces.
End-to-end security event processing pipeline of the
Intelligent SOC Ecosystem

Elastic Agent and Fleet collect raw logs from Firewall (pfSense), Linux Router, IDPS (Suricata), NSM (Zeek), WAF (ModSecurity). Logs are parsed, normalized to ECS standard and stored for pipeline processing.
SmartXDR Ingest Pipeline filters redundant fields, extracts contextual information, and generates the ml_input field - a structured, condensed log representation serving as input for ML classification.
SmartXDR Classification uses Bylastic (DistilBERT-based model by Byviz Analytics) to analyze ml_input semantically, assign severity labels, and generate prediction_probability scores stored in ml.prediction.* fields.
Elastic Detection Rules query ML fields for anomaly detection. ElastAlert2 monitors alerts index and forwards matched alerts with IoCs, timestamps, and Kibana links to DFIR-IRIS for case management.
Analysts review alerts in DFIR-IRIS, convert to Incident Cases. IntelOwl performs IoC pre-analysis via MISP and VirusTotal. SmartXDR Analysis uses RAG for intelligent interpretation and risk assessment.
n8n workflows orchestrate Wazuh Active Response for endpoint isolation, pfSense/Suricata rule updates for network blocking. SmartXDR Reporting generates DOCX reports, uploads to cloud storage, and sends Telegram notifications.
Watch our Intelligent SOC Ecosystem in action through real-world attack scenarios
Simulates a user opening a disguised PDF file on a Windows 11 workstation (192.168.85.150). The executable, camouflaged with a PDF icon, launches a background process and establishes a beacon connection to an external Command & Control (C2) server.
Watch DemoDemonstrates SQL Injection exploitation against DVWA web application behind ModSecurity WAF (192.168.85.111). The attacker targets the database server (192.168.85.112) to expose sensitive data, manipulate records, or escalate privileges.
Watch DemoAn attacker from the GUEST network (192.168.95.100) uses automated tools to perform password brute-forcing against SMB service on Windows Server (192.168.85.115), attempting NTLM authentication bypass for lateral movement.
Watch DemoSimulates social engineering attack where a user downloads a fake MediaPlayer installer (.zip) containing malware. Wazuh Agent detects the threat via VirusTotal integration, automatically removes the malicious file, and reports to the central system.
Watch DemoDemonstrates ChatOps workflow via Telegram integration. Administrators interact bidirectionally with SmartXDR through the chatbot, requesting AI-powered incident analysis or executing response actions directly from the messaging platform.
Watch DemoAccess demo videos and project documentation
The minds behind the Intelligent SOC Ecosystem

SOC Analyst
Specialized in SIEM, SOC operations, and advanced threat detection. Skilled in building centralized monitoring systems with ELK, Suricata, and security automation solutions.

SOC Analyst
Experienced in SOC workflows, SIEM systems, and threat detection techniques. Proficient in deploying ELK Stack, Suricata IDS/IPS, and creating automated security solutions.